Integration with Microsoft Exchange
Understand the basics of the integration of AskCody with Microsoft Exchange
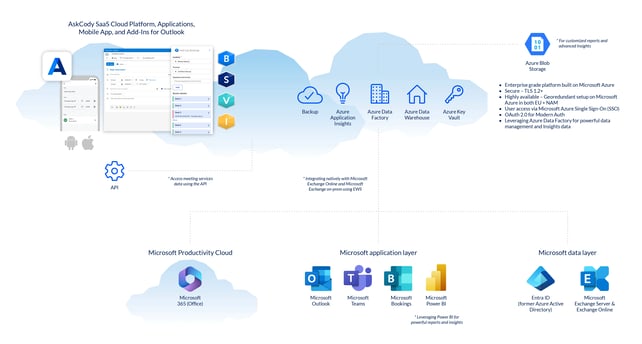
AskCody + Microsoft Exchange
AskCody is an intelligence layer on top of the Microsoft infrastructure and backbone integrating natively with Microsoft using Microsoft Exchange Webservices Managed API and integrates with and shares data using Microsoft EWS. Microsoft EWS is built-in and a native part of Microsoft Exchange and Microsoft Exchange Online that is used to share data with third parties like AskCody. Microsoft EWS, therefore, must be enabled and available for AskCody to access directly.
Integrating the AskCody Meeting Management Platform with your Microsoft Exchange Server or Exchange Online tenant (Office 365) is an important and key step in setting up AskCody. Therefore, it’s highly recommended that you spent some time understanding Microsoft Exchange, and how AskCody integrates with Exchange. This will help you understand the requirements when the integration between Exchange and AskCody will be established.
These articles highlight the overall concept of integrating AskCody with Microsoft Exchange.
The articles cover topics like:
- How AskCody integrates with Exchange
- How AskCody integrates with Exchange Meeting Room Resources
- What meeting data is accessible in Microsoft Exchange and what data AskCody process
- How to set up booking policies and scheduling permissions to comply with business policies and procedures
- How to integrate with Exchange using Basic Authentication or Modern Authentication (OAuth 2.0)
Further helpful reading on AskCody and Microsoft Exchange is:
- Basic Authentication vs. Modern Authentication and how these two types of authentication are different
- The difference between Impersonation and Delegation, and why Impersonation is required with AskCody
- Scoping Application Permissions with ApplicationImpersonation (Management Scope)
These articles go through important topics and highlight some frequently asked questions on AskCody and Microsoft Exchange in terms of security matters:
- Why ApplicationImpersonation is needed with Basic Auth and how ApplicationImpersonation is secure for application-level mailbox access.
- How audit logging and audit trails for a Service Account with Basic Auth can be managed for security purpose
- What the difference between Basic and Modern Auth is, how and when each should be used
- Who can use Modern Authentication instead of Basic Authentication
- Why using Modern Authentication requires a Global Admin account with a Mailbox authenticating the account the first time you sign up
- Why full access to mailboxes are needed with Modern Auth (OAuth 2.0)
- How to set up Application Scoping to limit Application Access (Management Scoping) for managing security levels with Microsoft Exchange
![Logo - Secondary White-1.png]](https://help.askcody.com/hs-fs/hubfs/Logo%20-%20Secondary%20White-1.png?height=50&name=Logo%20-%20Secondary%20White-1.png)